Security Questions
|
Security Quick Summary Summary of Human Security Vulnerabilities:
Reference: CCNA 200-301 Official Cert Guide Volume 2 Rivest-Shamir-Adleman (RSA) Characteristics RSA is a public-key encryption algorithm that uses an asymmetric encryption algorithm to encrypt data. Asymmetric encryption uses a key pair that is mathematically linked to encrypt and decrypt data. A private and public key are created, with the public key being accessible to anyone and the private key being a secret known only by the key pair creator. With RSA, either the private or public key can encrypt the data, while the other key decrypts it. This is one of the reasons RSA is the most used asymmetric encryption algorithm. |
Question 1
Explanation
This is a training program which simulates an attack, not a real attack (as it says “The webpage that opens reports that it was safe”) so we believed it should be called a “user awareness” program. Therefore the best answer here should be “user awareness”. This is the definition of “User awareness” from CCNA 200-301 Offical Cert Guide Book:
“User awareness: All users should be made aware of the need for data confidentiality to protect corporate information, as well as their own credentials and personal information. They should also be made aware of potential threats, schemes to mislead, and proper procedures to report security incidents. “
Note: Physical access control means infrastructure locations, such as network closets and data centers, should remain securely locked.
Question 2
Question 3
Explanation
In order to generate an RSA key for SSH, we need to configure the hostname and a DNS domain name on the router (a username and password is also required). Therefore in fact both answer C and answer D are correct.
Question 4
Question 5
Explanation
A site-to-site VPN allows offices in multiple fixed locations to establish secure connections with each other over a public network such as the Internet. A site-to-site VPN means that two sites create a VPN tunnel by encrypting and sending data between two devices. One set of rules for creating a site-to-site VPN is defined by IPsec.
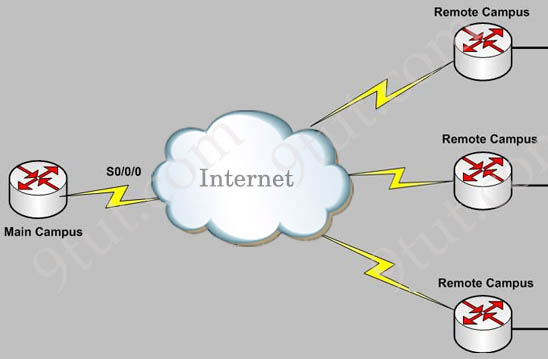
In the topology above, Remote Campus sites can connect to the Main Campus through site-to-site VPNs.
Question 6
Explanation
This is an example of how two-factor authentication (2FA) works:
1. The user logs in to the website or service with their username and password.
2. The password is validated by an authentication server and, if correct, the user becomes eligible for the second factor.
3. The authentication server sends a unique code to the user’s second-factor method (such as a smartphone app).
4. The user confirms their identity by providing the additional authentication for their second-factor method.
Question 7
Explanation
“enable secret” is the password that will be used to switch from User Exec mode to Priv Exec mode and it is always encrypted. It does not “prevent passwords from being stored in the configuration as plaintext” so this answer is not correct.
Question 8
Explanation
The “login local” command instructs the device to use the username and password in its local database for authentication. The secret is encrypted when it is stored on the local router.
Question 9
Explanation
The service password-encryption command will encrypt all current and future passwords so any password existed in the configuration will be encrypted.
Note: With the “service password-encryption” command, administrators can still configure clear-text passwords but they will be encrypted in the configuration file. So we cannot say “prevents network administrators from configuring clear-text passwords”.
Question 10
Explanation
A password manager only helps you remember your chosen passwords without typing them by yourself. It automatically fills into the password textbox for you so it does not provides a second authentication factor. An example of second authentication factor is an one time password (OTP) sent to your phone after typing your password and you have to type this OTP to authenticate.
By using a password manager, you are encouraged to create a complex password because you don’t need to remember it.
Question 11



q3
Which configuration is needed to generate an RSA key for SSH on a router?
A. Configure the version of SSH
B. Configure VTY access
C. Create a user with a password
D. Assign a DNS domain name
For generate rsa key user and pass is not needed…
only D is correct.
@q3 No, you must assign a DNS domain too.
“Which command prevents passwords from being stored in the configuration as plaintext on a router or switch?” I think correct answer is “B. enable secret”, because the question asks “PREVENTS passwords from being stored as plaintext”, not how encrypt password stored in plaintext.
Why Questions are not visible and only explanation is visible on this 9tut website
@Tem, this is the link to do the test related: https://www.9tut.com/security-quiz
Q8 sw2 and sw3 have the same configurations so what is the right answer
@9tut Q8 sw2 and sw3 have the same configurations so what is the right answer
@Arpan: Sw2 is configured with “password” (in “username admin1 password …” command) while Sw3 is configured with “secret” (in “username admin1 secret …” command) so they are different.
@9tut what would you recommend for someone self-studying for the CCNA 200-301?
would memorising all the questions under CCNA 200-201 do the job or do you need more than questions to be ready?
and are these questions from a previous 200-301 paper?