Security Questions 2
Question 1
Explanation
With “login local” command, the router will use the local username and password for authentication. And we assigned the highest privilege level of 15 for this user so we are put into privilege mode automatically (R1#).
Question 2
Question 3
Explanation
ARP attack (like ARP poisoning/spoofing, man-in-the-middle) is a type of attack in which a malicious actor sends falsified ARP messages over a local area network as ARP allows a gratuitous reply from a host even if an ARP request was not received. This results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network. This is an attack based on ARP which is at Layer 2. Dynamic ARP inspection (DAI) is a security feature that validates ARP packets in a network which can be used to mitigate this type of attack.
Question 4
Explanation
The Web Security appliance (WSA) intercepts requests that are forwarded to it by clients or other devices over the network. Proxy caching is a setting in WSA that caches data to increase performance.
Question 5
Explanation
In stateful inspection, the firewall not only inspects packets up through the application layer/layer7 determining a packet’s header information and data content, but also monitors and keeps track of the connection’s state. For all active connections traversing the firewall, the state information, which may include IP addresses and ports involved, the sequence numbers and acknowledgement numbers of the packets traversing the connection, TCP packet flags, etc. is maintained in a state table.
Question 6
Question 7
Explanation
VLAN Hopping: By altering the VLAN ID on packets encapsulated for trunking, an attacking device can send or receive packets on various VLANs, bypassing Layer 3 security measures. VLAN hopping can be accomplished by switch spoofing or double tagging. One of a popular type of VLAN Hopping is
Double-Tagging attack:
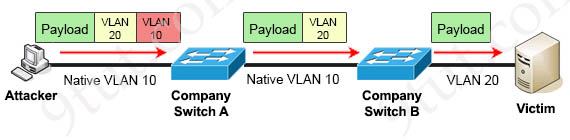
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed. Switch A forwards the frame out all links with the same native VLAN 10. Switch B receives the frame with an tag of VLAN 20 so it removes this tag and forwards out to the Victim computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker. In other words, this attack is only successful if the attacker belongs to the native VLAN of the trunk link. Another important point is, this attack is strictly one way as it is impossible to encapsulate the return packet.
To mitigate this type of attack, we can use VLAN access control lists (VACLs, which applies to all traffic within a VLAN. We can use VACL to drop attacker traffic to specific victims/servers); or implement Private VLANs; or keep the native VLAN of all trunk ports different from user VLANs.
Question 8
Explanation
The IEEE 802.1x standard defines a client-server-based access control and authentication protocol that prevents unauthorized clients from connecting to a LAN through publicly accessible ports unless they are properly authenticated. The authentication server authenticates each client connected to a switch port before making available any services offered by the switch or the LAN. Until the client is authenticated, 802.1x access control allows only Extensible Authentication Protocol over LAN (EAPOL), Cisco Discovery Protocol (CDP), and Spanning Tree Protocol (STP) traffic through the port to which the client is connected. After authentication is successful, normal traffic can pass through the port.



thanks @ 9tut
Can you explain Question 7?
can you explain Question 1 please? not question 7,my mistake
For question 1, why is D the answer? When I saw fresh switch I just assumed that transport input telnet had to be part of the command and
R1(config)#username admin privilege 15 secret p@ss1234
R1(config-if)#line vty 0 4
R1(config-line)#login local
also uses the word secret, which makes me think of ssh. I assumed B was the answer because of the transport input telnet.
Could anyone explain to me why B is not correct and D is? I’m probably just missing something.
DEAR TREVOR:
The TRANSPORT INPUT TELNET command forces the equipment to use TELNET only. it’s like if you type the TRANSPORT INPUT SSH command it will only use SSH or the TRANSPORT INPUT ALL command This command allows you to use both TELNET AND SSH and you can add the TRANSPORT INPUT NONE command to prevent the use of neither TELNET nor SSH
I am unable to see questions just the explanations