Security Questions 2
Question 1
Explanation
In fact in question wants to mention about site-to-site VPN. A site-to-site VPN allows offices in multiple fixed locations to establish secure connections with each other over a public network such as the Internet. A site-to-site VPN means that two sites create a VPN tunnel by encrypting and sending data between two devices. One set of rules for creating a site-to-site VPN is defined by IPsec.
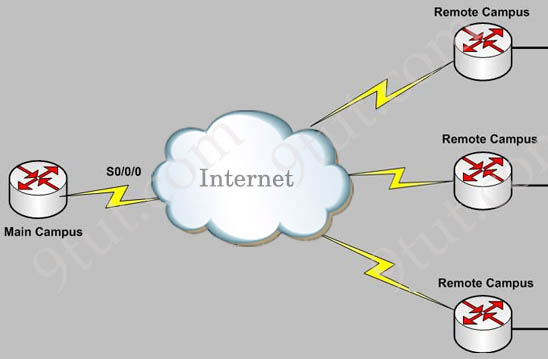
In the topology above, Remote Campus sites can connect to the Main Campus through site-to-site VPNs.
Question 2
Explanation
SSH, or secure shell, is a secure protocol that provides a built-in encryption mechanism for establishing a secured connection between two parties, authenticating each side to the other, and passing commands and output back and forth.
Note: Virtual Private Networks (VPNs) are only secure if encrypted. The word “private” only means a given user’s virtual network is not shared with others. In reality a VPN still runs on a shared infrastructure and is not secured if not encrypted. VPNs are used over a connection you already have. That might be a leased line. It might be an ADSL connection. It could be a mobile network connection.
Therefore answer “SSH” is still better than the answer “VPN”.
Question 3
Explanation
The “transport input” command is used to define which protocols to use to connect to a specific line (vty, console, aux…) of the router. The “transport input all” command will allow all protocols (including SSH and Telnet) to do this.
Question 4
Explanation
This question wants to ask how to use the router as the SSH client to connect into other routers. The table below shows the parameters used with SSH:
| SSH command parameters | Description |
| -v | specifies whether we are going to use version 1 or version 2 |
| -c {3des | aes128-cbc | aes192-cbc j aes256-cbc} | specifies the encryption you are going to use when communicating with the router. This value is optional; if you choose not to use it, the routers will negotiate the encryption algorithm to use automatically |
| -l username | specifies the username to use when logging in to the remote router |
| -m {hmac-md5 | hmac-md5-96 | hmac-sha1 | hmac-sha1-96} | specifies the type of hashing algorithm to use when sending your password. It is optional and if you do not use it, the routers will negotiate what type of hashing to use. |
| ip-address | hostname | we need to specify the IP address or, if you have DNS or static hostnames configured, the name of the router you want to connect to |
For example the command “ssh -v 2 -l admin 10.1.1.1” means “use SSH version 2 to connect to a router at 10.1.1.1 with username “admin”.
Answer C is not correct because it is missing the version needed to use.
Question 5
Question 6
Question 7
Explanation
When you connect to a switch/router via Telnet, you first need to provide Telnet password first. Then to access Privileged mode (Switch#) you need to provide secret password after typing “enable” before making any changes.
Question 9
Question 10
Explanation

(DHCP) Spoofing attack is a type of attack in that the attacker listens for DHCP Requests from clients and answers them with fake DHCP Response before the authorized DHCP Response comes to the clients. The fake DHCP Response often gives its IP address as the client default gateway -> all the traffic sent from the client will go through the attacker computer, the attacker becomes a “man-in-the-middle”.
The attacker can have some ways to make sure its fake DHCP Response arrives first. In fact, if the attacker is “closer” than the DHCP Server then he doesn’t need to do anything. Or he can DoS the DHCP Server so that it can’t send the DHCP Response.
VLAN Hopping: By altering the VLAN ID on packets encapsulated for trunking, an attacking device can send or receive packets on various VLANs, bypassing Layer 3 security measures. VLAN hopping can be accomplished by switch spoofing or double tagging.
1) Switch spoofing:

The attacker can connect an unauthorized Cisco switch to a Company switch port. The unauthorized switch can send DTP frames and form a trunk with the Company Switch. If the attacker can establish a trunk link to the Company switch, it receives traffic to all VLANs through the trunk because all VLANs are allowed on a trunk by default.
(Instead of using a Cisco Switch, the attacker can use a software to create and send DTP frames).
2) Double-Tagging:
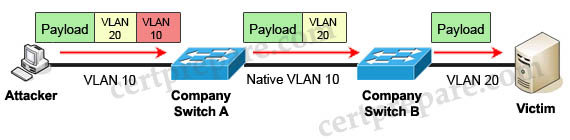
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed. Switch A forwards the frame out all links with the same native VLAN 10. Switch B receives the frame with an tag of VLAN 20 so it removes this tag and forwards out to the Victim computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker.
ARP attack (like ARP poisoning/spoofing) is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network. This is an attack based on ARP which is at Layer 2.
Question 11
Explanation
802.1x is an IEEE Standard for port-based Network Access Control (PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN.
Question 12
Explanation
IPsec is a pair of protocols, Encapsulating Security Payload (ESP) and Authentication Header (AH), which provide security services for IP datagrams.
ESP can provide the properties authentication, integrity, replay protection, and confidentiality of the data (it secures everything in the packet that follows the IP header).
AH provides authentication, integrity, and replay protection (but not confidentiality) of the sender.
Question 13
Which two statements about stateful firewalls in an enterprise network are true? (Choose two)
A. They are more susceptible to DoS attacks than stateless firewalls
B. They can filter HTTP and HTTPS traffic in the inbound direction only
C. They are most effective when placed in front of the router connected to the internet
D. They can track the number of active TCP connections
E. They can use information about previous packets to make decisions about future packets
Answer: D E
Explanation
The stateful firewall (with ASA being in that category) monitors the state of each TCP connection from the time the first TCP connection initiation request is sent using a SYN packet, and tracking the state of the connection like the packet sequence and TCP flags looking for any deviations or anomalies in the TCP connection state and blocking them.
Although a TCP connection is a bi-directional connection, the stateful firewall keeps track of the initiator of the TCP connection, thus adding directionality to a TCP connection. A stateful firewall allows connections in one direction (for example, TCP destination port 80 for a web server) only by default and maintains a state table that also records the random TCP source port used by the client, as a part of the connection state. Such firewalls that treat the bidirectional communications of a TCP connection as a single connection and maintain the current state of connections are called stateful firewalls -> This allows tracking of future packets through the established connection -> Answer E is correct.
Some firewalls monitor the traffic in each direction without maintaining any state of the TCP connections, but monitoring traffic as per the defined security policies. Such firewalls are called stateless firewalls.
Reference: Implementing Cisco Networking Solutions Book by Harpreet Singh
In stateful inspection, the firewall not only inspects packets up through the application layer/layer7 determining a packet’s header information and data content, but also monitors and keeps track of the connection’s state. For all active connections traversing the firewall, the state information, which may include IP addresses and ports involved, the sequence numbers and acknowledgement numbers of the packets traversing the connection, TCP packet flags, etc. is maintained in a state table (-> answer D is correct). Filtering decisions are based not only on rules but also on the connection state established by prior packets on that connection. This enables to prevent a variety of DoS, DDoS, and other security violations -> stateful firewall is effective for Dos, DDos attack -> Answer A is not correct.



I would like to know if 9tut allows to prepare for the CCNA Security exam