Drag Drop Questions 2
Question 1
Question 2
Question 3
Explanation
From the ACL:
access-list 107 deny tcp 207.16.12.0.0.0.3.255 any eq http
access-list 107 permit ip any any
We can deduce it block all source hosts in 207.16.12.0/22 range (which ranges from 207.16.12.0 to 207.16.15.255) via HTTP (port 80) while permit any other hosts.
Question 4
Explanation
There are four messages sent between the DHCP Client and DHCP Server: DHCPDISCOVER, DHCPOFFER, DHCPREQUEST and DHCPACKNOWLEDGEMENT. This process is often abbreviated as DORA (for Discover, Offer, Request, Acknowledgement).
Question 5
Explanation
1: connected (AD = 0)
2: static (AD = 1)
3: EBGP (AD = 20)
4: EIGRP (AD = 90)
5 :OSPF (AD = 110)
6: RIP (AD = 120)
Question 6
Explanation
Traditional Networking uses block list model because all traffic is allowed to pass through initially until we configure an ACL, prefix-list… This model is more lenient, because if no application knowledge exists, the default network configuration will let everything through. From a security perspective, it is very dangerous though – every time you allow a protocol that the application does not need, you are unnecessarily increasing your attack surface, and therefore compromising the overall application security.
In Controller-Based Networking, everything is denied by default until we explicitly allow them by a white (allow) list.
Question 7
Explanation
VLAN Hopping: By altering the VLAN ID on packets encapsulated for trunking, an attacking device can send or receive packets on various VLANs, bypassing Layer 3 security measures. VLAN hopping can be accomplished by switch spoofing or double tagging.
a. Switch spoofing:

The attacker can connect an unauthorized Cisco switch to a Company switch port. The unauthorized switch can send DTP frames and form a trunk with the Company Switch. If the attacker can establish a trunk link to the Company switch, it receives traffic to all VLANs through the trunk because all VLANs are allowed on a trunk by default.
(Instead of using a Cisco Switch, the attacker can use a software to create and send DTP frames).
To mitigate this type of attack, we can disable DTP.
b. Double-Tagging attack:
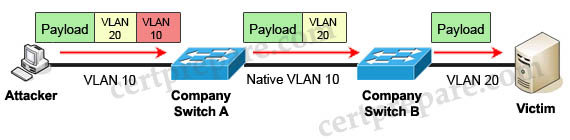
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed. Switch A forwards the frame out all links with the same native VLAN 10. Switch B receives the frame with an tag of VLAN 20 so it removes this tag and forwards out to the Victim computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker.
To mitigate this type of attack, we can use VLAN access control lists (VACLs, which applies to all traffic within a VLAN. We can use VACL to drop attacker traffic to specific victims/servers) or implement Private VLANs.
Question 8
Explanation
A typical enterprise hierarchical LAN campus network design includes the following three layers:
+ Access layer: Provides workgroup/user access to the network
+ Distribution layer: Provides policy-based connectivity and controls the boundary between the access and core layers
+ Core layer: Provides fast transport between distribution switches within the enterprise campus
Reference: https://www.ciscopress.com/articles/article.asp?p=2202410&seqNum=4
Question 9
Question 10
Explanation
In the output above, three lines under “Link-local IPv6 Address” line have been blacked out so we have to figure out what they are. They are the IP address of the Wireless card and the Default gateway of this computer.



Question 2 is missing the Broadcast addresses in column 2, As well as missing the answers for which addresses are match
@Zane: In fact question 2 is correct. The right columns are for Broadcast addresses only and we had four answers for this question:
Answer:
+ 10.63.255.255/10
+ 172.16.255.39/29
+ 172.20.255.255/16
+ 192.168.255.127/25
in the drag and drop the order when dragging comes the same as it appears in 9 tut?
I think the answer of question 8 is wrong. the conditions must be switched like that
Distribution layer:
+ functions as an aggregator for all the campus blocks
Core layer:
+ establishes Layer 3 routing boundaries functions
you know that from the Reference: https://www.ciscopress.com/articles/article.asp?p=2202410&seqNum=4
it is written below ….
Oh.. sorry my mistake
@9tut Looks like the MAC Adress in Question 10 is wrong.
@zane for Q2
10.1.255.254/24 IP address is 10.1.255.254 sub net mask is 255.255.255.0 so board cast address should be 10.1.255.255 not 254 so this is wrong
10.63.255.255/10 IP address is 10.63.255.255 sub net mask is 255.192.0.0 so board cast is 256-192=64 64-1 is 63 so board cast address is 10.63.255.255 this is correct
/29 =255.255.255.248 /16 =255.255.0.0 /25 =255.255.255.128 for this 3 the board cast IP address is equal to board cast address so choose these
access-list 107 deny tcp 207.16.12.0.0.0.3.255 any eq http
This is NOT a valid command. You need to have a space before the wildcard mask. I believe the IOS may attempt to query a DNS server using the string of character that are not valid.
Not only is there no space between the address and wildcard mask, but there is actually a period that strangely connects the two values.