DHCP Snooping Tutorial
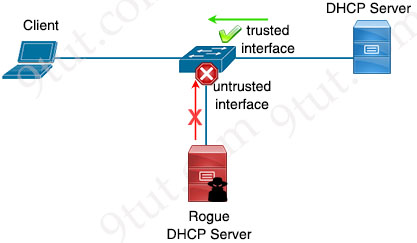
DHCP Snooping is a Layer 2 security feature that can be configured on a switch to listen DHCP traffic and block DHCP OFFER and DHCP ACK packets (which can only be sent from a DHCP server) on untrusted ports.
DHCP Snooping is very easy to configure. We only need to:
1. Turn this feature on the switch
2. Configure trusted interface(s). Other interfaces are untrusted by default.
Trusted interface is the interface that is connected to our DHCP server so that all DHCP messages are allowed.
DHCP Snooping feature also creates a table of IP – MAC address mapping which lists client MAC addresses, DHCP-assigned IP addresses…
Configure DHCP Snooping
Configure DHCP Snooping is very simple. We just need to:
1. Turn on DHCP Snooping feature
2. Configure trusted interfaces
We will use the same topology as above. We added interface labels for the configuration:
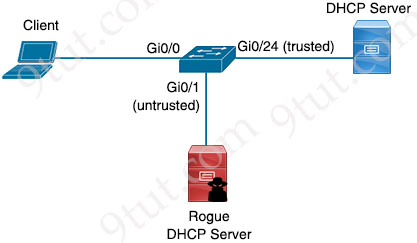
In our example, the DHCP server is connected to the port Gi0/24. So we will configure DHCP snooping to allow Offer/ACK messages only on this port.
Switch(config)#ip dhcp snooping //turn on DHCP Snooping feature globally on all VLANs on the switch Switch(config-if)#interface Gi0/24 Switch(config-if)#ip dhcp snooping trust
That’s all for the configuration! If you want to turn on DHCP Snooping on a specific VLAN only, use the “ip dhcp snooping vlan {vlan-id}” instead.
Now if our switch receives any DHCP Offer or DHCP ACK messages from Gi0/1 interface then it will ignore them.
We can also check which IP addresses have been assigned to which devices (MAC addresses) with the “show ip dhcp snooping binding” command.
Switch#show ip dhcp snooping binding NO. MACADDRESS IPADDRESS LEASE(SEC) TYPE VLAN INTERFACE --- ------------ -------- ------- ---------- ----- ----------------- 1 00:A3:D1:44:20:46 10.0.0.3 85556 DHCP-Snooping 1 GigabitEthernet0/0 Total number of bindings: 1
From the output, we see our client (with MAC address of 00:A3:D1:44:20:46 has been assigned an IP address of 10.0.0.3 by DHCP on Gi0/0 interface.


