CCNA – Drag and Drop 1
Here you will find answers to drag and drop Questions
Question 1:
A dental firm is redesigning the network that connects its three locations. The administrator gave the networking team 192.168.164.0 to use for addressing the entire netwok. After subnetting the address, the team is ready to assign the addresses. The administrator plans to configure ip subnet-zero and use RIP v2 as the routing protocol. As a member of the networking team, you must address the network and at the same time conserver unused addresses for future growth. With those goals in mind, drag the host addresses on the left to the correct router interface. Once of the routers is partially configured. Move your mouse over a router to view its configuration. Not all of the host addresses on the left are necessary.
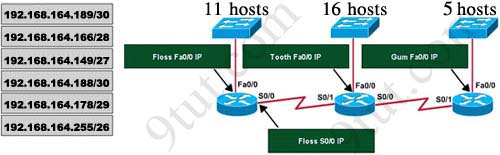
Answer:
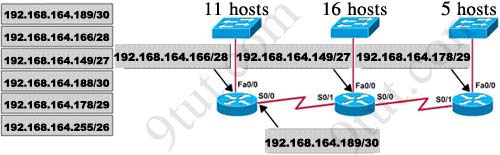
Explanation:
In short, we should start calculating from the biggest network (with 16 hosts) to the smallest one using the formula 2n – 2 (n is the number of bits we need to borrow).Therefore:
16 hosts < 25 – 2 (we need to borrow 5 bits -> /27)
11 hosts < 24 – 2 (borrow 4 bits -> /28)
5 hosts < 23 – 2 (borrow 3 bits -> /29)
From the available ip addresses, we see that each of them has only one suitable solution (they are 192.168.164.149/27,192.168.164.166/28 and 192.168.164.178/29)
The smallest network is the Floss S0/0 which only requires 2 hosts = 22 – 2 (need to borrow 2 bits ->/30). There are 2 suitable answers: 192.168.164.189/30 and 192.168.164.188/30 but notice that 192.168.164.188/30 is the network address so we can not use it (because 188 = 4 * 47) -> we have to choose 192.168.164.189 as the correct solution.
In fact, it is not the formal way to solve a VLSM question so I recommend you to review your CCNA book if you haven’t grasped it well yet.
Question 2:
In order to complete a basic switch configuration, drag each switch IOS command on the left to its purpose on the right
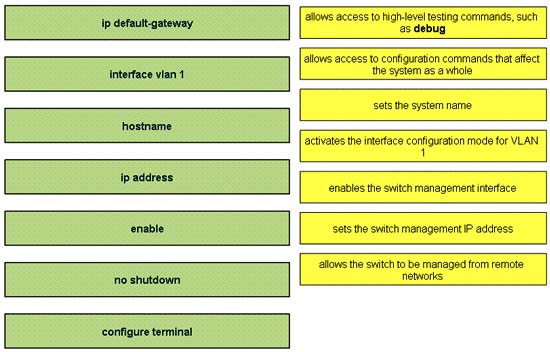
Answer:
1) enable
2) configure terminal
3) hostname
4) Interface vlan 1
5) no shutdown
6) ip address
7) ip default-gateway
Question 3:
The Missouri branch office router is connected through its s0 interface to the Alabama Headquarters router s1 interface. The Alabama router has two LANs. Missouri users obtain Internet access through the Headquarters router. The network interfaces in the topology are addressed as follows: Missouri: e0 – 192.168.35.17/28; s0 – 192.168.35.33/28; Alabama: e0 – 192.168.35.49/28; e1 – 192.168.35.65/28; s1 – 192.168.35.34/28. The accounting server has the address of 192.168.35.66/28. Match the access list conditions on the left with the goals on the right. (Not all options on the left are used.)
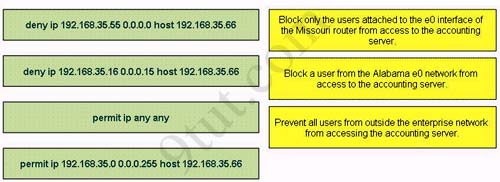
Answer:
1) deny ip 192.168.35.16 0.0.0.15 host 192.168.35.66
2) deny ip 192.168.35.55 0.0.0.0 host 192.168.35.66
3) permit ip 192.168.35.0 0.0.0.255 host 192.168.35.66
Explanation:
1) The wildcard mask of the command “deny ip 192.168.35.16 0.0.0.15 host 192.16.35.66” is 0.0.0.15, which is equal to network mask of 255.255.255.240 = /28. So the access list will deny all traffic from network 192.168.35.16/28 from accessing host 192.16.35.66, which is the IP address of accounting server.
2) The command “deny ip 192.168.35.55 0.0.0.0 host 192.168.35.66” will deny host 192.168.35.55, which is a user and belongs to interface e0 of Alabama router (192.168.35.49/28) from accessing accounting server.
3) Because there is an implicit “deny all” command at the end of each access list so the command “permit ip 192.168.35.0 0.0.0.255 host 192.168.35.66” will only let network 192.168.35.0/24 access accounting server whilst prevent traffic from other networks.
Question 4:
A host with the address of 192.168.125.34/27 needs to be denied access to all hosts outside its own subnet. To accomplish this, complete the command in brackets, [access-list 100 deny protocol address mask any], by dragging the appropriate options on the left to their correct placeholders on the right.
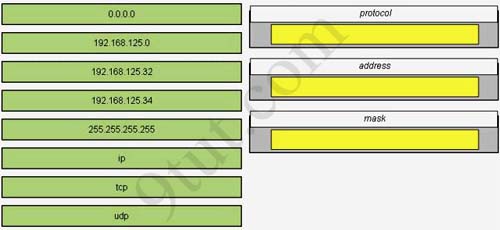
Answer:
1) ip
2) 192.168.125.34
3) 0.0.0.0
Full command: access-list 100 deny ip 192.168.125.34 0.0.0.0
Question 5:
Drag and drop the network user application to the appropriate description of its primary use (not all options are used)
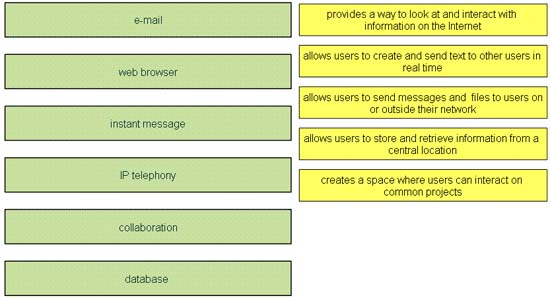
Answer:
1) web browser
2) instant message
3) e-mail
4) database
5) collaboration
Question 6:
This topology contains 3 routers and 1 switch. Complete the topology.
| Drag the appropriate device icons to the labeled Device
Drag the appropriate connections to the locations labeled Connections. Drag the appropriate IP addresses to the locations labeled IP address |
(Hint: use the given host addresses and Main router information)
To remove a device or connection, drag it away from the topology.
Use information gathered from the Main router to complete the configuration of any additional routers. No passwords are required to access the Main router . The config terminal command has been disabled for the HQ router. The router does not require any configuration.
Configure each additional router with the following
| Configure the interfaces with the correct IP address and enable the interfaces.
Set the password to allow console access to consolepw Set the password to allow telnet access to telnetpw Set the password to allow privilege mode access to privpw |
Note: Because routes are not being added to the configurations, you will not be able to ping through the internetwork.
All devices have cable autosensing capabilities disabled.
All hosts are PC’s
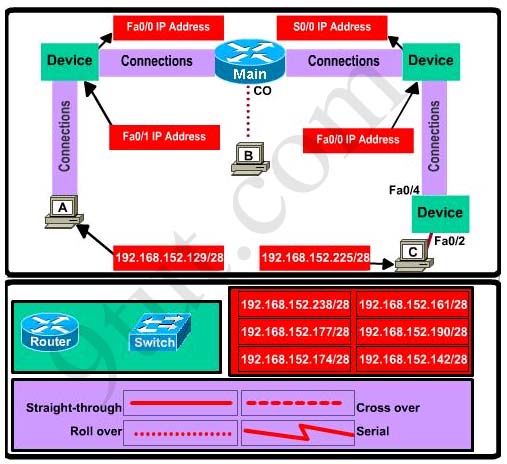
Answer:
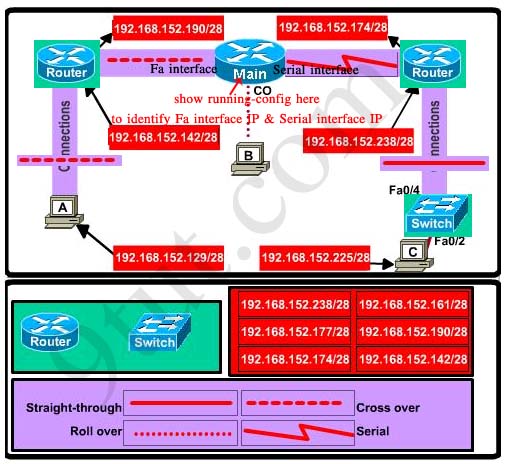
View full explanation of this question here


