Access List Tutorial
In this tutorial we will learn about access list.
Access control lists (ACLs) provide a means to filter packets by allowing a user to permit or deny IP packets from crossing specified interfaces. Just imagine you come to a fair and see the guardian checking tickets. He only allows people with suitable tickets to enter. Well, an access list’s function is same as that guardian.
Access lists filter network traffic by controlling whether packets are forwarded or blocked at the router’s interfaces based on the criteria you specified within the access list.
To use ACLs, the system administrator must first configure ACLs and then apply them to specific interfaces. There are 3 popular types of ACL: Standard, Extended and Named ACLs.
Standard IP Access List
Standard IP lists (1-99) only check source addresses of all IP packets.
Configuration Syntax
| access-list access-list-number {permit | deny} source {source-mask} |
Apply ACL to an interface
| ip access-group access-list-number {in | out} |
Example of Standard IP Access List
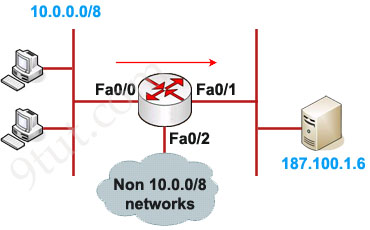
Configuration:
In this example we will define a standard access list that will only allow network 10.0.0.0/8 to access the server (located on the Fa0/1 interface)
Define which source is allowed to pass:
Router(config)#access-list 1 permit 10.0.0.0 0.255.255.255
(there is always an implicit deny all other traffic at the end of each ACL so we don’t need to define forbidden traffic)
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 1 out
The ACL 1 is applied to permit only packets from 10.0.0.0/8 to go out of Fa0/1 interface while deny all other traffic. So can we apply this ACL to other interface, Fa0/2 for example? Well we can but shouldn’t do it because users can access to the server from other interface (s0 interface, for example). So we can understand why an standard access list should be applied close to the destination.
Note: The “0.255.255.255” is the wildcard mask part of network “10.0.0.0”. We will learn how to use wildcard mask later.
Extended IP Access List
Extended IP lists (100-199) check both source and destination addresses, specific UDP/TCP/IP protocols, and destination ports.
Configuration Syntax
| access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port] |
Example of Extended IP Access List
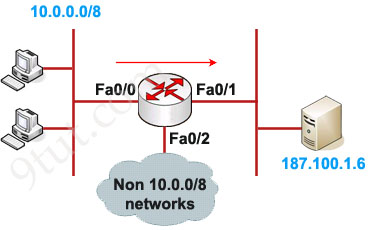
In this example we will create an extended ACL that will deny FTP traffic from network 10.0.0.0/8 but allow other traffic to go through.
Note: FTP uses TCP on port 20 & 21.
Define which protocol, source, destination and port are denied:
Router(config)#access-list 101 deny tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 21
Router(config)#access-list 101 deny tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 20
Router(config)#access-list 101 permit ip any any
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 101 out
Notice that we have to explicit allow other traffic (access-list 101 permit ip any any) as there is an “deny all” command at the end of each ACL.
As we can see, the destination of above access list is “187.100.1.6 0.0.0.0” which specifies a host. We can use “host 187.100.1.6” instead. We will discuss wildcard mask later.
In summary, below is the range of standard and extended access list
| Access list type | Range |
| Standard | 1-99, 1300-1999 |
| Extended | 100-199, 2000-2699 |



Marvelous, what a weblog it is! This website provides helpful information to
us, keep it up.
Thanks for sharing your thoughts. I really appreciate your efforts and I am waiting
for your next write ups thanks once again.
Hi, after reading this amazing paragraph i am as well glad to share my familiarity here
with friends.
Hello, the rule of thumb is.
first deny then anything else is permitted right?
@9 tut: Regarding your Extended Access List example, isn’t it better to implement the Extended ACL closest to the source / traffic to be matched? (so that you can prevent unnecessary bandwidth usage as the frame would be sent all the way down to the destination if you choose Fa0/1, rather than dropping it closest to the source at Fa0/0).
In this case, interface Fa0/0 and apply ACL as: ip access-group 101 in (instead of out) ?
where are the questions May you please provide link
True ….. Extended ACL are best done close to the source to eliminate unnecessary bandwidth consumption.
This is perfect dude, keep it up!
So is the Extended IP Access-list example wrong? You set the access-list closet to the destination (Fa0/1) instead of closet to the source (Fa0/0).
@9tut – I agree the Extended ACL should be FA0/0 in not fa0/1 out.
Hi, as far as I know, the Extended ACLs should be applied closest to the source f0/0 in this case, could someone CONFIRM IT.
If someone could give an example of an Extended ACL applied in OUTBOUND direction would be much appreciated.
amazing
i would not use the fa0/1 in the last example in page1. if you put your ACL on that interface all traffic would be processed. Why not using the int fa0/0 inbound?
It would be inappropriate to block traffic at Fa0/0 when the question says we block it only from accessing 187.100.1.6 and not to Non 10.0.0.0/8 Networks where it may be needed and has to go through Fa0/0. That’s my opinion.
One of the best explainings for ACLs imho
“maximum: 0001111 = 31)” – is there one missing 1? I mean 31 should be: 00011111
@Artiom: Thank you for your detection, we updated it!