AAA TACACS+ and RADIUS Tutorial
Nowadays, security plays an important role in a company. Without any security solution implementation on our network, a user can simply “plug and play” into our network. The user may simple pick up a valid IP address or be assigned one automatically via DHCP. It is convenient, but not a good way if your network contains sensitive data. Worse, this user may have all the rights to your network so he can do dangerous things.
When your company grows bigger and bigger, there is a moment that you need to consider implementing security to your network. There are many ways to secure a network but AAA offers a complete solution. In this tutorial let’s find out about this security feature.
Before diving into AAA, let’s take an example of a user who wants to connect to our network.
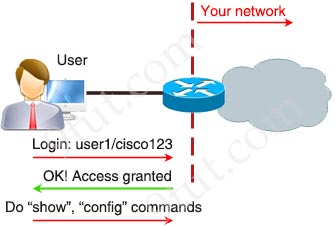
This process uses a login and password on the access line. Although it is very easy to implement, but there are many disadvantages of using this method:
+ Insecure login method
+ Vulnerable to brute-force attacks
+ No accountability
+ Must be configured on each device manually
+ Store usernames & passwords locally on each device
+ Cannot limit which specific commands are not used
With AAA, now the process of a user connecting to our network is shown below:
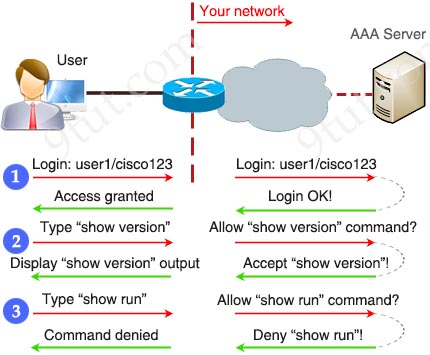
Every action the users do must be submitted to the AAA server to determine if they are allowed or not. This process has many advantages:
+ Secure login (AAA server is not exposed to users and only some protocols are allowed to be sent initially)
+ Easy management at one or some centralized servers
+ Firewalls or other security devices can be placed before AAA servers to protect them
+ Can accept or reject specific commands
+ Every command typed by users can be logged for later analysis
Disadvantages:
+ Require powerful server (to handle all the traffic and requests)
AAA stands for Authentication, Authorization and Accounting.
+ Authentication: Specify who you are (usually via login username & password)
+ Authorization: Specify what actions you can do, what resource you can access
+ Accounting: Monitor what you do, how long you do it (can be used for billing and auditing)
An example of AAA is shown below:
+ Authentication: “I am a normal user. My username/password is user_tom/learnforever“
+ Authorization: “user_tom can access LearnCCNA server via HTTP and FTP“
+ Accounting: “user_tom accessed LearnCCNA server for 2 hours“. This user only uses “show” commands.
With AAA, users must authenticate before getting an IP address to access the network. Otherwise, they can only use specific protocols to continue authenticating
For authentication we can do via local database, 802.1x standard (which was developed to provide a method to authenticate devices attempting to access a switchport/LAN) or via remote AAA servers. There are two popular client/server AAA protocols to communicate between remote AAA servers and authenticating devices:
+ RADIUS (Remote Authentication Dial In User Service)
+ TACACS+ (Terminal Access Controller Access-Control System)
The comparison of two protocols is listed below:
| RADIUS | TACACS+ | |
| Transportation & Ports |
UDP port 1812/1645 (Authentication) 1813/1646 (Accounting) |
TCP port 49 |
| Encryption | only passwords | entire payload of each packet (leaving only the TACACS+ header in cleartext) |
| Standards | Open standard | Cisco proprietary (but actually now it is an open standard defined by RFC1492) |
| Operation | Authentication and authorization are combined in one function (packet) | authentication, authorization and accounting are separated |
| Logging | No command logging | Full command logging (commands typed by users can be recorded on the servers) |
Note:
+ RADIUS is very old protocol (created around the early 1990s) and it was originally designed for dial-in modem connections. In these old days, security is not a strong concern so RADIUS encrypts only the authentication information (passwords) along the traffic path.
+ TACACS+ is a newer version of TACAS and XTACAS. It is the answer of Cisco to RADIUS.
+ Both RADIUS and TACACS+ support Extensible Authentication Protocol (EAP), which is an authentication framework frequently used in wireless networks and point-to-point connections
+ Both TACACS+ and RADIUS can run on either Windows or Unix/Linux servers
+ TACACS+ separates the authentication, authorization, and accounting steps. This architecture allows for separate authentication solutions while still using TACACS+ for authorization and accounting.
+ Authentication and authorization are not separated in a RADIUS transaction. When the authentication request is sent to a AAA server, the AAA client expects to have the authorization result sent back in reply.
+ TACACS+ supports access-level authorization for commands. That means you can assign privilege levels when a user logins successfully.
In the next part we will learn how to configure AAA.



hi everyone, hopefully someone can help my exam, Please sned my latest dump of 200-125 exam at ehrgs30atgmaildotcom
I have my exam in a week and would like the latest dumps for the 200-125 to test my knowledge.
cynthia.fritz123 at gmail dot com
Passed my exam yesterday. sims ipv6 Ospf, access-list and a lot of drag and drop
Please share your latest dumps with me tosinosu @ yahoo.com
can anyone share the latest dumps with me. masmusta at hotmail dot com
hi everyone, please help me share the latest dump for ccna 200-125 {email not allowed}
hi everyone, please help me share the latest dump for ccna 200-125 thurain568 at gmail . com
Anyone may help me and share the latest dump for ccna at — pecchiacchio @ gmail . com
need latest ccna dump plz. masazmus at yahoo dot fr
please share latest dump with me too… {yashodharajagalgoda @ gmail .com }
if anyone have the latest ccna dumps please send me my mail is umerraheem6gmail.com
if anyone have the latest CCNA dumps in VCE please send me my mail is {email not allowed}
if anyone have the latest CCNA dumps in VCE please send me my mail is moxz757 @ gmail.com
Please share the latest dumps for ccna 200-125 to {email not allowed}.
Please share the latest dumps for ccna 200-125 to wesly.w3st at gmail.com
Please share the latest dumps for ccna 200-125 to {email not allowed}
Please share the latest dumps for ccna 200-125 to rebeccaowhigho @ gmail.com
Please share the ccna latest dumps with me
Rodgihan @ gmail.com
I sell ccna latest dump (jan2020) certbus(vce file + software) price is 10$(not give free please dont write about it) write me ilknur(dot)nasirzadeh(at) gmail(dot) com
Please share the latest dumps for ccna 200-125
skupljamparezalondon @ gmail . com
Please share the last dumps for 200-105 ICND2 mail4melg @ gmail . Com
hi everyone, please help me share the latest dump for ccna 200-125 ogirimayahaya1 at gmail . com
Could anyone send me the latest dump for ccna 200-125, please? ayenyeinthuzar @ gmail dot com
Could you any provide the latest dump CCNA exam ? I am writing my exam on the Feb 12. any help would be appreciated.
please forward any details to email {email not allowed}
Regards
JF
hi everyone, please help me share the latest dump for ccna 200-125 elvioktm @ gmail dot com
Can someone please send exam vce dumps for ccna routing and switching to {email not allowed}
Send to jzus18@ aol .com
pleas send dumps for Feb 15th dpadewilson @ outlook dot com
High guys!
I would be very glad if someone shared with me some recent dumps.
Sincerely,
Sean
P.S. Hope everyone will pass! {email not allowed}
Hi guys!
I would be very glad if someone shared with me some recent dumps.
alshynov @ gmail com
Sincerely,
Sean
P.S. Hope everyone will pass!