Port Security Tutorial
By default, all interfaces on a Cisco switch are in an enabled state, meaning that anyone can potentially connect to your network through a wall socket, posing a security risk. Port Security is a feature that enhances the security of Cisco switches by controlling access to Ethernet ports based on the MAC addresses of connected devices.
Port Security allows network administrators to associate only specific MAC addresses or set a maximum number of MAC addresses with each switch port. This association restricts access to the interface, ensuring that only authorized devices with recognized MAC addresses can use it. If an unauthorized device attempts to connect, you can configure the switch to take predefined actions, such as discarding the incoming traffic, sending a warning message or shutting down the port to mitigate the security threat.
In the figure below, only host with MAC address of AAA (just for example. In fact the MAC address must be 48 bits) was configured to connect to the switch port while other MAC addresses are blocked:
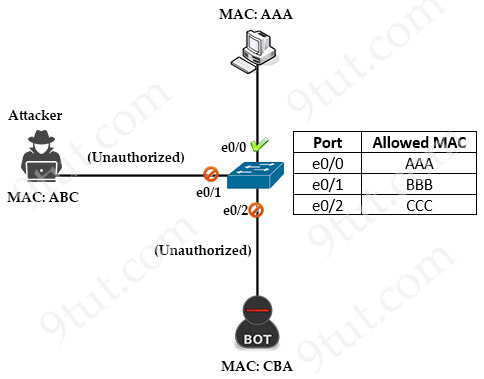
Configuring port security
There are three steps to configure port security on a Cisco switch:
1. Configure the switch port as an access port using the “switchport mode access” command.
2. Activate port security on the switch port with the “switchport port-security” command.
3. Specify the permitted MAC addresses for sending frames through the interface. This can be done by utilizing either the “switchport port-security mac-address {MAC_Address}” command or, for dynamic MAC address learning, the “switchport port-security mac address sticky” command while the host is connected. An example of the configuration is shown below:
Switch(config)#interface e0/1 Switch(config-if)#switchport mode access Switch(config-if)#switchport port-security Switch(config-if)#switchport port-security mac-address aaaa.aaaa.aaaa
This is the minimum configuration to activate port-security.
To verify the port-security configuration on an interface, we can use the “show port-security interface {interface}” command:
Switch#show port-security interface Ethernet0/0 Port Security : Enabled Port Status : Secure-up Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 1 Last Source Address:Vlan : AAAA.AAAA.AAAA:1 Security Violation Count : 0
There are two optional steps for more control of this feature:
1. Specify the action the switch should take when it receives a frame from an unauthorized device using the “switchport port-security violation {protect/restrict/shutdown}” command.
+ Protect: drops the packets with an unknown source MAC address. It will not make log entry for dropped packets. Interface will learn MAC address until it reaches the maximum allowed number of MAC address that was configured. Any additionally learned addresses would be dropped while keeping interface operational.
+ Restrict: drops the packets with unknown source MAC addresses. It then causes the SecurityViolation counter to increase and generate a security violation alert.
+ Shutdown: causes the interface to enter an error-disabled state (same as down state) immediately. It then sends an SNMP trap notification. The switchport will remain in this state until manually removed. This is the default violation mode.
All three options result in discarding traffic from the unauthorized device. Both the “restrict” and “shutdown” options also generate log messages when a violation occurs, with the “shutdown” mode additionally disabling the port.
2. Set the maximum allowable number of MAC addresses that can be used on the port using the “switchport port-security maximum {number}” interface command. The default number of MAC addresses allowed is 1 so if we connect another host to the same port, the security violation will occur and the port is put into err-disabled state:
First we will receive an error message like this when we try to connect another host (with MAC 0090.ab0e.4582) to this port (through another switch or hub):
%PM-4-ERR_DISABLE: psecure-violation error detected on Et0/0, putting Et0/0 in err-disable state %PORT_SECURITY-2-PSECURE_VIOLATION: Security violation occurred, caused by MAC address 0090.ab0e.4582 on port Ethernet0/0. %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/0, changed state to down %LINK-3-UPDOWN: Interface Ethernet0/0, changed state to down
Then we can check this port to see it is in err-disabled state:
Switch#show interfaces Ethernet0/0 Ethernet0/0 is down, line protocol is down (err-disabled)
Err-disabled state is same as “shutdown” state. But it means the security violation occurred on this port.
Also the port-security on this port:
Switch#show port-security interface Et0/0 Port Security : Enabled Port Status : Secure-shutdown Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 1 Sticky MAC Addresses : 0 Last Source Address:Vlan : 0090.ab0e.4582:1 Security Violation Count : 1
The line “Port Status: Secure-shutdown” means that this port has been shut down because of port-security. We can reactivate this port by using the “shutdown” and “no shutdown” commands.
Summary
Port security is a good feature in Cisco devices for securing access to your network through a switch. By following the steps outlined in this tutorial, you can configure, manage, and troubleshoot port security to enhance the security of your network and prevent unauthorized access.



Mac address 128 bit? may be an error. the correct is 48 bits
@FJCZ: Thank you for your detection, we fixed it!
i am not bot
Hate nit picking about terminology, but if there is anything I’ve learned on this website, it’s to be crystal clear about terms and acronyms.
+ Protect: drops the packets with an unknown source MAC address. It will not make log entry for dropped packets. Interface will learn MAC address until it reaches the maximum allowed number of MAC address that was configured. Any additionally learned addresses would be dropped while keeping interface operational.
+ Restrict: drops the packets with unknown source MAC addresses. It then causes the SecurityViolation counter to increase and generate a security violation alert.
+ Shutdown: causes the interface to enter an error-disabled state (same as down state) immediately. It then sends an SNMP trap notification. The switchport will remain in this state until manually removed. This is the default violation mode.
Switches that manage port-security DO NOT analyze network packets. They analyze frames. I see this wording on here a lot where frames and packets are seemingly used interchangeably and it’s causing quite a bit of confusion for me.
hello, has anyone had any luck verifying if port security in pack tracer with non allowed host mac?
I configured the port security, but when testing another mac address that is not allowed it doesn’t shut down the port.